India’s Aadhaar program has garnered attention worldwide for creating the largest biometric database globally. Despite being marketed as voluntary, its expanding indispensability and legal frameworks have effectively made it mandatory. This analysis delves into the social and legal dimensions surrounding Aadhaar, juxtaposing them with data privacy and biometric collection principles from the European Union and the United States. It advocates for aligning Aadhaar’s privacy framework with the principles of necessity and consent, primarily through forthcoming national data privacy legislation. Emphasizing the significance of privacy rights and individual interests, particularly in a program where consent underpins data collection and in a nation where privacy holds constitutional sanctity, is paramount.
Structure of the Aadhaar System and Database:
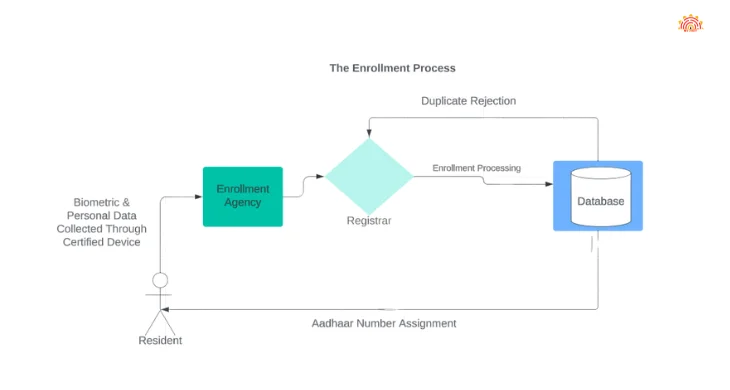
The Aadhaar system involves multiple entities and processes in data collection, processing, and storage. Registrars, enrollment agencies, and the Unique Identification Authority of India (UIDAI) play key roles. Residents provide personal information and biometric data at enrollment centers, which is then forwarded to registrars for de-duplication. Upon completion, data is stored in the Central Identities Data Repository (CIDR), and residents receive unique Aadhaar numbers.
Data Purging and Opt-Out Options:
Once enrolled, there’s no provision for resident data purging from the Aadhaar database. The system relies on this data for de-duplication and uniqueness confirmation. While residents have the option to not enroll initially, there’s no mechanism for data removal post-enrollment, except for specific cases such as children reaching adulthood.
Addressing Resident Grievances:
The UIDAI establishes a Contact Centre to manage queries and grievances, serving as a central point of contact for residents, registrars, and enrollment agencies. Residents receive enrollment acknowledgment forms containing an Enrolment Number for query purposes.
Access to UID Database and Security Measures:
Aadhaar number holders are entitled to access their information in the UID database. CIDR operations adhere to strict access protocols to limit database access. Stringent security measures, including encryption during data transit and severe penalties for security breaches, safeguard the database against cyber threats.
Protective Measures and Privacy:
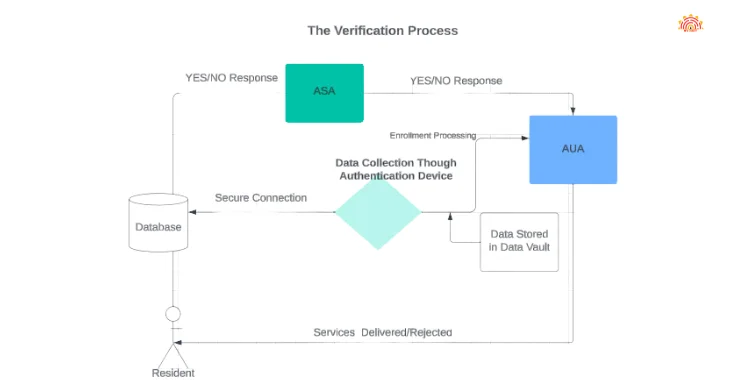
The UIDAI collects limited information necessary for Aadhaar issuance and identity confirmation, refraining from profiling or tracking sensitive personal data. It only responds with a ‘yes’ or ‘no’ to identity verification requests, except in specific instances such as court orders or national security imperatives. Robust data protection policies and strict access controls ensure data security and confidentiality.
Convergence and Data Linkages:
The UID database operates independently, solely for identity verification purposes with consent. It’s securely guarded physically and electronically, with access restricted to authorized personnel. Data convergence with other databases is prohibited, ensuring data integrity and privacy.
Conclusion:
Upholding individual rights and ensuring data protection within India’s Aadhaar system necessitates a delicate balance between necessity, consent, and stringent privacy measures. As Aadhaar continues to evolve, aligning its framework with international privacy standards while preserving individual liberties remains imperative.
FAQ
Ques. Can the occupant’s data be purified from Aadhaar database?
Ans. As is the case with the other services providedfrom the government, there’s no provision for purifying the data of the occupant from the database once he has attained his Aadhaar. The data is also needed as it’s used forde-duplication of every new entrant in the database against all the being records to establish the oneness of the occupant. Only after this process is completed that the Aadhaar is assigned.
Ques. Can a occupant conclude out of Aadhaar?
Ans. The occupant has the option in the first case not to enrol for Aadhaar at all. Aadhaar is a service delivery tool, and not designed for any other purpose. Aadhaar being unique to every occupant isnon-transferable. still, it’ll remain dormant, as the use is grounded on the physical presence and biometric authentication of the person, If the occupant doesn’t wish to use the Aadhaar. still, children, within 6 months of attaining maturity, may make an operation for cancellation of their Aadhaar as per the vittles of the Aadhaar Act, 2016( as amended) and regulations framed there under.
Ques. How will the grievances of the occupant be addressed?
Ans. The UIDAI’ll set up a Contact Centre to manage all queries and grievances that serve as a single point of contact for the association. The details of the Contact Centre will be published on the website as and when registration begins. The druggies of this system are anticipated to be residers, registers and registration agencies. Any occupant seeking registration is given a published acknowledgement form with an Registration Number, that enables the occupant to make queries about her/ his registration status through any communication channel of the contact centre. Each registration agency will be given a unique law that will also enable briskly and refocused access to the Contact Centre that includes a specialized helpdesk.
Ques. Who’ll have access to the UID database? How will the security of the database be assured?
Ans. Residers who have aadhaar figures will be entitled to pierce their own information stored in the UID database.CIDR operations will be follow strict access protocols to limit access to the database.The database itself will be secured against hacking and other forms of cyberattacks.
Ques. How does the UIDAI cover the individual and their information?
Ans. Protection of the existent, and the securing their information is essential in the design of the UID design. From having a arbitrary number which doesn’t reveal anything about the individual to other features listed below, the UID design keeps the interest of the occupant at the core of its purpose and objects.
Collecting limited information
Data collected by the UIDAI is purely to issue Aadhaar figures, and confirm the identity of Aadhaar number holders. The UIDAI is collecting introductory data fields in order to be suitable to establish identity – this includes Name, Date of Birth, Gender, Address, Parent Guardian’s name essential for children but not for others, mobile number and dispatch id is voluntary as well. The UIDAI is collecting biometric information to establish oneness – thus collecting print, 10 cutlet prints and iris.
No profiling and tracking information collected
The UIDAI policy bars it from collecting sensitive particular information similar as religion, estate, community, class, race, income and health. The profiling of individualities is thus not possible through the UID system, since the data collected is limited to that needed for identification and identity evidence. The UIDAI had in fact, dropped the ‘ place of birth ’ data field – part of the original list of information it planned to collect – grounded on feedback from CSOs that it could lead to profiling. The UIDAI also doesn’t collect any sale records of the existent. The records of an individual attesting their identity through Aadhaar will only reflect that such a evidence happed. This limited information will be retained for a short period time in the interest of the occupant, to resolve any controversies.
Release of information
The UIDAI is barred from revealing particular information in the Aadhaar database – the only response permitted are a ‘ yes ’ or ‘ no ’ to requests to corroborate an identity. The only exceptions are the order of a court, or the order of a joint clerk, in case of public security. This is a reasonable exception and is clear and precise. This approach is also in line with security morals followed in US and Europe on access to data in case of a security trouble.
Data protection and confidentiality
The UIDAI has the obligation to insure the security and confidentiality of the data collected. The data will be collected on software handed by the UIDAI and translated to help leaks in conveyance. Trained and certified enrollers will collect the information, which won’t have access to the data being collected.
The UIDAI has a comprehensive security policy to insure the safety and integrity of its data. It’ll publish further details on this, including the Information Security Plan and programs for the CIDR and mechanisms for auditing the compliance of the UIDAI and its constricting agencies. In addition, there will be strict security and storehouse protocols in place. Penalties for any security violation will be severe, and include penalties for telling identity information. There will also be correctional consequences for unauthorised access to CIDR – including hacking, and penalties for tampering with data in the CIDR.
Confluence and linking of UIDAI information to other databases
The UID database isn’t linked to any other databases, or to information held in other databases. Its only purpose will be to corroborate a person’s identity at the point of entering a service, and that too with the concurrence of the aadhaar number holder. The UID database will be guarded both physically and electronically by a many select individualities with high concurrence. It’ll not be available indeed for numerous members of the UID staff and will be secured with the stylish encryption, and in a largely secure data vault. All access details will be duly logged.

